 ADFS (SAML SSO)
ADFS (SAML SSO)
Mar 6, 2022
Want to use Active Directory Federation Services (ADFS) for your Single Sign-On? Pipeline can integrate with your SAML Identify Provider (IdP). Follow this solution guide to setup this integration.
Want the automation but not the hassle of setup and maintenance?
With Managed integrations, we'll do all the heavy-lifting, so that you can focus on more important things!
Prerequisites
You will the following before you can enable SAML SSO for Windows ADFS:
- Windows Active Directory Federation Server
- Pipeline: Custom Single Sign-On addon
Configure Your ADFS
Add Pipeline as a Relying Party Trust
To add Pipeline as a Relying Party Trust:
- Open AD FS Management → Trust Relationships → Relying Party Trust and select Add Relying Party Trust
- On Select Data Source, select
Import data about the relying party...

Enter
https://[your_instance]/signin/saml-getspmetadata.aspx - On Specify Display Name, the imported name is
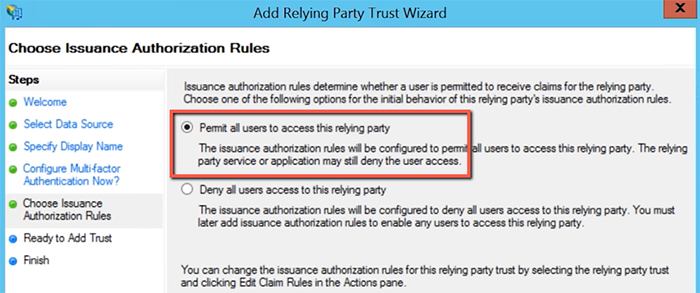
[your_instance]. You may change it to confirm with your naming standards, ex:Pipeline ADFS SSO. - On Choose Issuance Authorization Rules, select
Permit all users to access this relying party
- After adding, open the Edit Claim Rules dialog:

Configure Claim Rules
Open the Issuance Transform Rules tab:

Create Rule to Map LDAP Attributes
- Click Add Rule and use the
Send LDAP Attributes as Claimsrule template

- Create rule
Send LDAP Attributesand map the following LDAP attributes to the outgoing claims:

- Click Finish to complete the rule.
Create Rule for Incoming Claims
- Click Add Rule and use the
Transform an Incoming Claimrule template

- Create rule
Email to NameIDwith the following settings:

- Incoming claim type
E-Mail Address - Outgoing claim type
Name ID - Outgoing name ID format
Email
- Incoming claim type
- Click Finish to complete the rule.
Download Federation XML and Signing Certificate
After you made the configurations, download the ADFS XML and the Signing Certificate.
Download the Federation Services XML
Open AD FS Management → Service → Endpoints and verify the location of FederationMetadata.xml

You should be able to download the file via your browser: https://[your_ADFS_server]/FederationMetadata/2007-06/FederationMetadata.xml
Download the Signing Certificate
- Open AD FS Management → Service → Certificates and select the Token-signing Certificate

- Select Details → Copy to File. Export as
Base-64 encoded X.509 (.CER)

- Click Finish to export the certificate.
Send the above ADFS information and the signing certificate our support help desk or in-app chat to integrate Pipeline with your ADFS SSO.
-
Windows: Create a Relying Party Trust
To add a new relying party trust by using the AD FS Management snap-in and manually configure the settings, perform the following procedure on a federation server. -
Windows: Create a Rule to Send LDAP Attributes as Claims
Using the Send LDAP Attributes as Claims rule template in Active Directory Federation Services (AD FS), you can create a rule that will select attributes from a Lightweight Directory Access Protocol (LDAP) attribute store, such as Active Directory, to send as claims to the relying party. -
Windows: Create a Rule to Transform an Incoming Claim
By using the Transform an Incoming Claim rule template in Active Directory Federation Services (AD FS), you can select an incoming claim, change its claim type, and change its claim value.